質問 1:Service Consumer A sends a message to Service A.
Before the message arrives with Service A, it is intercepted by Service Agent A (1). which checks the message for
compliance to Policy A that is required by Service A.
If the message fails compliance, Service Agent A will not allow it to proceed and will instead write the message contents to a
log. If the message does comply to the policy, it continues to be transmitted toward Service
A, but before it arrives it is intercepted by Service Agent B (2), which validates the security
credentials in the message header. If the security credential validation fails, the message is
rejected and a runtime exception is raised. If the security credentials are validated, the
message is sent to Service A.
Upon receiving the message, Service A retrieves a data value from a database and
populates the message header with this data value (3) prior to forwarding the message to
Service B.
Before the message arrives at Service B.
it is intercepted by Service Agent C (4) which checks the message for compliance with two policies: Policy B and Policy C.
Policy
B is identical to Policy A that was checked by Service Agent A.
To check for compliance to Policy C.
Service Agent C uses the data value added by Service A.
If the message complies with both of the policies, it is forwarded to Service B (5), which stores the message contents in its own database.

You are told that Policy B and Policy C have changed. Also, in order to carry out the
compliance check of Policy C, Service Agent C will now require a new data value from the
Service B database. How can this service composition architecture be changed to fulfill
these new requirements?
A. The Policy Centralization pattern can be applied so that only one service agent is used
to enforce Policy A and Policy B.
Service Consumer A is redesigned to first query Service
B for the value required by Service Agent C.
This way, Service Consumer A can include this value in the message header prior to sending the message to Service A .
B. The Policy Centralization pattern can be applied so that only one service agent is used
to enforce Policy A and Policy B.
The policy enforcement logic for Policy C is removed from
Service Agent C and instead embedded within the logic of Service B . This way, Service B
can itself retrieve the value required to check compliance with Policy C.
If the message received is not in compliance, Service B will reject it.
C. None of the above.
D. The Policy Centralization pattern can be applied so that only one service agent is used
to enforce Policy A and Policy B.
Service A is redesigned to first query Service B for the value required by Service Agent C to check the compliance of the updated Policy C.
If the compliance check is successful, the message is sent to Service B .
正解:C
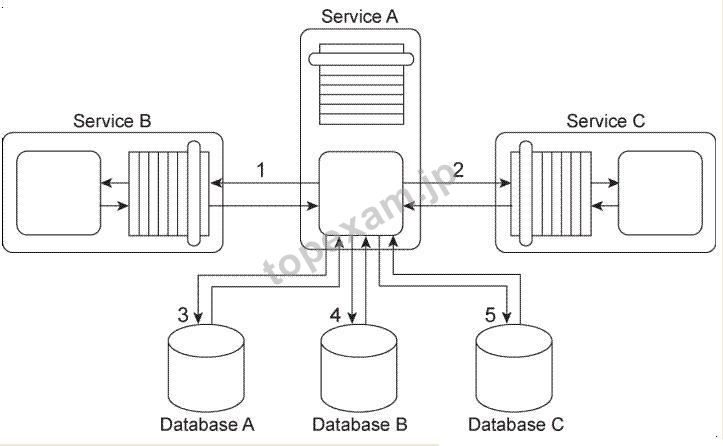
質問 2:Service A is an entity service that provides a set of generic and reusable service
capabilities. In order to carry out the functionality of any one of its service capabilities,
Service A is required to compose Service B (1) and Service C (2) and Service A is required
to access Database A (3), Database B (4), and Database C (5). These three databases are
shared by other applications within the IT enterprise.
All of service capabilities provided by Service A are synchronous, which means that for
each request a service consumer makes. Service A is required to issue a response
message after all of the processing has completed.
Depending on the nature of the service consumer request, Service A may be required to
hold data it receives in memory until its underlying processing completes. This includes
data it may receive from either Service A or Service B or from any of the three shared
databases.
Service A is one of many entity services that reside in a highly normalized service
inventory. Because Service A provides agnostic logic, it is heavily reused and is currently
part of many service compositions.

You are told that Service A has recently become unstable and unreliable. The problem has
been traced to two issues with the current service architecture. First, Service B, which is
also an entity service, is being increasingly reused and has itself become unstable and
unreliable. When Service B fails, the failure is carried over to Service A . Secondly, shared
Database B has a complex data model. Some of the queries issued by Service A to shared
Database B can take a very long time to complete. What steps can be taken to solve these
problems without compromising the normalization of the service inventory?
A. The Redundant Implementation pattern can be applied to Service B, thereby making
duplicate deployments of the service available. This way, when one implementation of
Service B is too busy, another implementation can be accessed by Service A instead. The
Service Data Replication pattern can be applied to establish a dedicated database that
contains an exact copy of the data from shared Database B that is required by Service A .
B. The Redundant Implementation pattern can be applied to Service A, thereby making
duplicate deployments of the service available. This way, when one implementation of
Service A is too busy, another implementation can be accessed by service consumers
instead. The Service Data Replication pattern can be applied to establish a dedicated
database that contains an exact copy of the data from shared Database B that is required
by Service A .
C. None of the above.
D. The Redundant Implementation pattern can be applied to Service B, thereby making
duplicate deployments of the service available. This way, when one implementation of
Service B is too busy, another implementation can be accessed by Service A instead. The
Service Data Replication pattern can be applied to establish a dedicated database that
contains a copy of the data from shared Database B that is required by Service A . The
replicated database is designed with an optimized data model in order to improve query
execution performance.
正解:D
質問 3:Service A is an orchestrated task service that is invoked by a separate composition initiator
(1) and then sends a request message to Service C (2). Service C queries Database B to
retrieve a large data record (3) and provides this data in a response message that is sent
back to Service A.
Service A temporarily stores this data in a central state database (4) and
then sends a request message to Service D (5), which accesses a legacy system API to
retrieve a data value (6). Service D then sends this data value in a response message back
to Service A.
The data in the state database is subsequently retrieved by Service A (7) and
merged with the newly received data value. This combined data is written to Database A
(8), which triggers an event that results in the invocation of Service B (9).
Service B is an orchestrated task service that sends a request message to Service D (10).
which accesses a legacy system API to retrieve a data value (11) and then sends this data
value in a response message back to Service B.
Service B temporarily stores this data in a
central state database (12) and then sends a request message to Service E (13), which
performs a runtime calculation and then responds with the calculated data value back to
Service B.
The data in the state database is then retrieved by Service B (14) and merged
with the calculated data value. Service B then uses the merged data to complete its
business task.
The following specific problems and requirements exist:
* Database B uses a proprietary data format that is not compliant with the XML
format used by all of the services in this service composition architecture This
incompatibility needs to be solved in order to enable the described service
message exchanges.
* The service contract provided by Service D does not comply with the data model
standards that were applied to the other services and therefore uses a different
data model to represent the same type of data that is exchanged. This
incompatibility needs to be solved in order to enable communication with Service
D.
* Database B is a shared database that can be accessed by other services and
applications within the IT enterprise, which causes unpredictable runtime
performance. This performance problem needs to be solved in order to make the
runtime behavior of Service C more predictable.
* For performance and maintenance reasons, Service A and Service B need to be
deployed in the same physical environment where they can share a common state
database.

Upon reviewing these requirements it becomes evident to you that the Enterprise Service
Bus compound pattern will need to be applied. However, there are additional requirements
that need to be fulfilled. To build this service composition architecture, which patterns that
is not associated with the Enterprise Service Bus compound pattern need to also be
applied? (Be sure to choose only those patterns that relate directly to the requirements
described above. Patterns associated with the Enterprise Service Bus compound pattern
include both the required or core patterns that are part of the basic compound pattern and
the optional patterns that can extend the basic compound pattern.)
A. State Repository
B. Policy Centralization
C. Reliable Messaging
D. Service Data Replication
E. Intermediate Routing
F. Process Centralization
G. Compensating Service Transaction
H. Atomic Service Transaction
I. Data Format Transformation
J. Data Model Transformation
K. Protocol Bridging
L. Event-Driven Messaging
M. Redundant Implementation
正解:A,D,F
質問 4:You are told that in this service composition architecture, all four services are exchanging
invoice-related data in an XML format. The services in Service Inventory A are
standardized to use a specific XML schema for invoice data. Design standards were not
applied to the service contracts used in Service Inventory B, which means that each
service uses a different XML schema for the same kind of data. Database A and Database
B can only accept data in the Comma Separated Value (CSV) format and therefore cannot
accept XML formatted data. What steps can be taken to enable the planned data exchange
between these four services?
 A.
A. The Data Model Transformation pattern can be applied so that data model
transformation logic is positioned between Service A and Service C . The Protocol Bridging
pattern can be applied so that protocol bridging logic is positioned between Service A and
Service B and between the Service C and Service D . The Data Format Transformation
pattern can be applied so that data format transformation logic is positioned between the
Service B logic and Database A and between the Service D logic and Database B.
B. The Data Model Transformation pattern can be applied so that data model
transformation logic is positioned between Service A and Service B, between Service A
and Service C, and between Service C and Service D . The Data Format Transformation
pattern can be applied so that data format transformation logic is positioned between the
Service B logic and Database A and between the Service D logic and Database B.
C. None of the above.
D. The Data Model Transformation pattern can be applied so that data model
transformation logic is positioned between Service A and Service C and between Service C
and Service D . The Data Format Transformation pattern can be applied so that data
format transformation logic is positioned between the Service B logic and Database A and
between the Service D logic and Database B.
正解:B



 PDF版 Demo
PDF版 Demo









 品質保証TopExamは我々の専門家たちの努力によって、過去の試験のデータが分析されて、数年以来の研究を通して開発されて、多年の研究への整理で、的中率が高くて99%の通過率を保証することができます。
品質保証TopExamは我々の専門家たちの努力によって、過去の試験のデータが分析されて、数年以来の研究を通して開発されて、多年の研究への整理で、的中率が高くて99%の通過率を保証することができます。 一年間の無料アップデートTopExamは弊社の商品をご購入になったお客様に一年間の無料更新サービスを提供することができ、行き届いたアフターサービスを提供します。弊社は毎日更新の情況を検査していて、もし商品が更新されたら、お客様に最新版をお送りいたします。お客様はその一年でずっと最新版を持っているのを保証します。
一年間の無料アップデートTopExamは弊社の商品をご購入になったお客様に一年間の無料更新サービスを提供することができ、行き届いたアフターサービスを提供します。弊社は毎日更新の情況を検査していて、もし商品が更新されたら、お客様に最新版をお送りいたします。お客様はその一年でずっと最新版を持っているのを保証します。 全額返金弊社の商品に自信を持っているから、失敗したら全額で返金することを保証します。弊社の商品でお客様は試験に合格できると信じていますとはいえ、不幸で試験に失敗する場合には、弊社はお客様の支払ったお金を全額で返金するのを承諾します。(
全額返金弊社の商品に自信を持っているから、失敗したら全額で返金することを保証します。弊社の商品でお客様は試験に合格できると信じていますとはいえ、不幸で試験に失敗する場合には、弊社はお客様の支払ったお金を全額で返金するのを承諾します。( ご購入の前の試用TopExamは無料なサンプルを提供します。弊社の商品に疑問を持っているなら、無料サンプルを体験することができます。このサンプルの利用を通して、お客様は弊社の商品に自信を持って、安心で試験を準備することができます。
ご購入の前の試用TopExamは無料なサンプルを提供します。弊社の商品に疑問を持っているなら、無料サンプルを体験することができます。このサンプルの利用を通して、お客様は弊社の商品に自信を持って、安心で試験を準備することができます。
